
Research
TIOCSTI injection
Abusing TIOCSTI to manipulate process file descriptors and execute arbitrary commands.
Browse all articles in Hacking

Abusing TIOCSTI to manipulate process file descriptors and execute arbitrary commands.
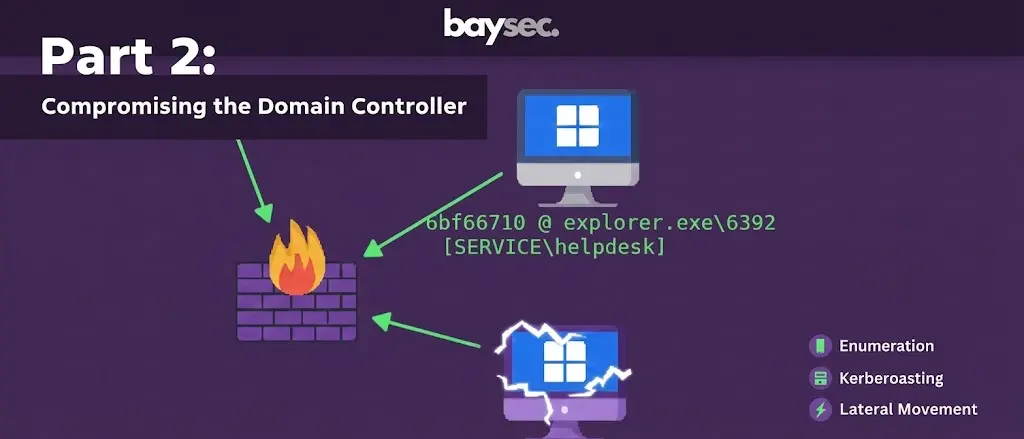
Exploiting the Active Directory environment and compromising the domain controller.
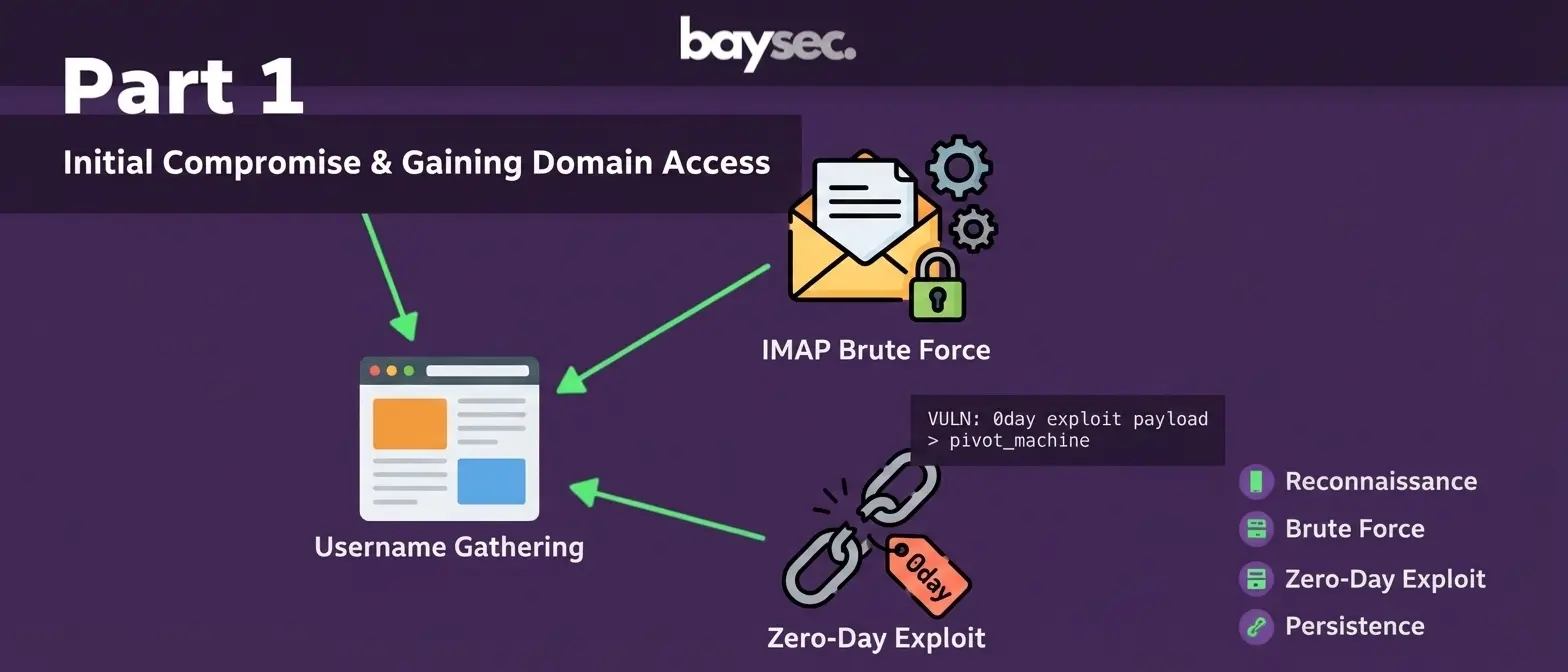
Finding a way into the internal infrastructure. Prototype pollution, popping shells, for fun, and for profit.

What happens when you run scripts without checking the contents properly?

This article will explain some of the common HTTP state interception methods.