Poland Cyber Threat Assessment - January 2026
Comprehensive analysis of Russian hybrid warfare operations targeting Poland. Intelligence derived from Baysec CTI and open-source reporting.
Table of Contents
- BLUF (Bottom Line Up Front)
- Executive Summary
- Credential Exposure
- Geopolitical Context
- Targeted Organizations - January 2026
- ICS/SCADA Access Claims - January 2026
- Threat Actors
- Threat Actor Details
- Campaign Analysis
- Threat Landscape: December 2025 → January 2026
- MITRE ATT&CK Mapping
- Sources and References
- Confidence Levels
BLUF (Bottom Line Up Front)
In December 2025, Sandworm (GRU Unit 74455) deployed DynoWiper against Polish energy infrastructure. Throughout January 2026, 40+ pro-Russian threat actors targeted 50+ Polish organizations across defense, energy, and government sectors. Key actors NoName057(16) and Z-PENTEST ALLIANCE have confirmed GRU ties per DOJ December 2025 indictments.
Executive Summary
Poland faces coordinated Russian hybrid warfare operations combining physical sabotage, destructive malware, and sustained cyber activity. This assessment covers January 2026 cyber operations, December 2025 DynoWiper attack and past physical sabotage for broader context. (Marywilska arson, railway attacks).
The January operations show coordination beyond typical hacktivism: systematic sector rotation (government → defense → energy), multi-group same-day targeting, and timing correlated with geopolitical events. DDoS activity provides visible disruption while ICS access claims and ransomware represent more significant capability development.
Key Findings
| Finding | Details |
|---|---|
| DynoWiper attack | Sandworm (GRU) deployed destructive wiper against Polish energy grid (Dec 2025) |
| Physical sabotage | GRU: Marywilska fire; FSB: railway sabotage, 30-person network disrupted |
| Hybrid warfare surge | 4x increase in Russian sabotage operations in 2024; 219 incidents since 2014, 86% since 2022 |
| Scale | 40+ threat actors targeted 50+ Polish organizations |
| Defense targeting | 7 Polish Armaments Group subsidiaries targeted in 48 hours (13-14 JAN) |
| ICS/SCADA claims | 10+ access claims including heating systems, water treatment |
| Ransomware | 5 confirmed Polish victims (Dec 2025-Jan 2026) |
| State nexus | Key actors (NoName057(16), Z-PENTEST/CARR) GRU-linked per DOJ indictments |
| Credential exposure | 50,000+ Polish domain credentials identified in infostealer logs |
Key Assessments
| Assessment | Confidence | Basis |
|---|---|---|
| Operations are coordinated, beyond independent hacktivism | HIGH | Sequential sector targeting; multi-group same-day operations |
| Threat actors possess capabilities beyond DDoS | HIGH | Documented data exfiltration, ICS access claims, ransomware |
| State direction for key actors | HIGH | DOJ indictments confirm GRU funding/direction for CARR/Z-PENTEST, NoName057(16) |
| Timing correlates with geopolitical events | MODERATE | Activity surged after PM Tusk’s attribution and Polish Consulate Odessa strike |
Credential Exposure
Stolen credentials represent a persistent threat enabling future intrusions.
In a sample of recent infostealer logs, we identified credentials for 50,000+ Polish domains - companies, banks, healthcare, government, financial services, energy, defense. This includes both government employee credentials and Polish citizen credentials for government service portals.
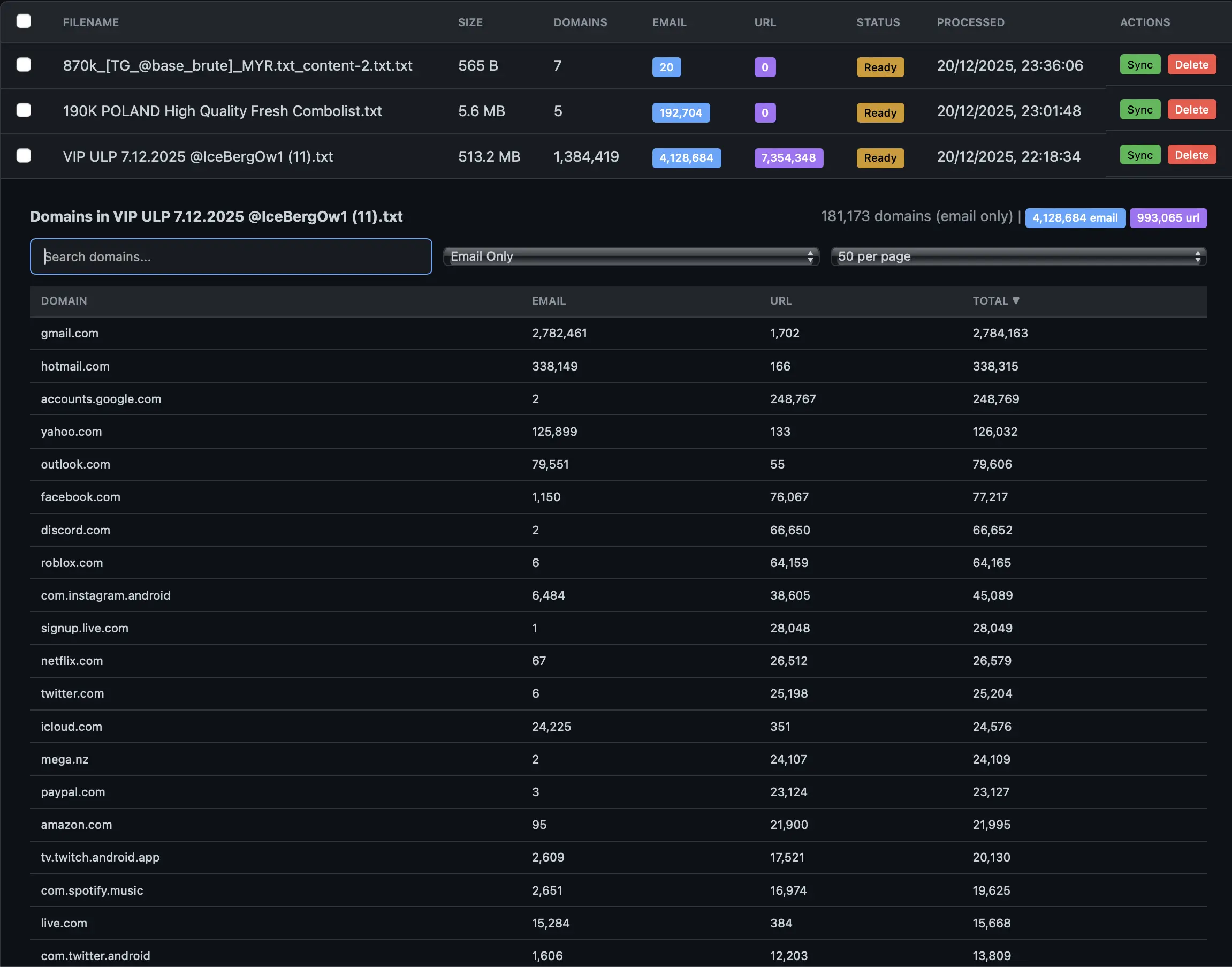 A single infostealer dump: 4.1 million credentials across 1.38 million domains.
A single infostealer dump: 4.1 million credentials across 1.38 million domains.
Polish credentials harvested by infostealers (RedLine, Raccoon, Vidar, LummaC2) are actively traded on Russian-language forums and Telegram. These credentials will be tested against Polish systems. Attackers exploit credential reuse across VPNs, email, cloud services, and internal systems.
Examples of Polish credential listings on Russian-language Telegram channels:
 Telegram channel sharing Polish credential dump
Telegram channel sharing Polish credential dump
 Telegram channel sharing Polish credential dump
Telegram channel sharing Polish credential dump
 Telegram post advertising Polish credentials
Telegram post advertising Polish credentials
 Telegram channel sharing Polish credential dump
Telegram channel sharing Polish credential dump
 Telegram channel sharing Polish credential dump
Telegram channel sharing Polish credential dump
 Telegram “cloud” channel distributing fresh infostealer logs.
Telegram “cloud” channel distributing fresh infostealer logs.
 Telegram credential channels are frequently banned, but new ones emerge within hours.
Telegram credential channels are frequently banned, but new ones emerge within hours.
Geopolitical Context
Russia’s Hybrid Warfare Campaign
Russia has dramatically escalated hybrid warfare operations against Poland and Europe since 2022. Per IISS analysis, sabotage operations increased 4x in 2024 compared to previous years. GLOBSEC research documented 219 Russian hybrid warfare incidents since 2014, with 86% occurring since 2022.
Three Pillars of Russian Hybrid Warfare:
| Pillar | Methods | Poland Examples |
|---|---|---|
| Subversion | Information manipulation, election interference, narrative warfare | Polish election disinformation |
| Coercion | Military posturing, energy leverage, economic pressure | Belarus border crisis; pre-2022 gas dependency |
| Sabotage | Physical attacks, infrastructure destruction | Marywilska fire, railway sabotage |
Physical Sabotage Timeline (2024-2026)
| Date | Operation | Details | Attribution | Source |
|---|---|---|---|---|
| May 2024 | Marywilska Shopping Center Fire | Warsaw’s largest shopping center destroyed; 1,400+ shops, €500M+ damage | GRU | Notes From Poland |
| Nov 2025 | Railway Sabotage | FSB-directed sabotage via recruited Ukrainian proxies | FSB | BBC |
| Dec 2025 | Mirgorodsky Network | 30-person FSB sabotage network disrupted; included arson, reconnaissance | FSB | Reuters |
| 29-30 Dec 2025 | Energy Grid Attack (DynoWiper) | Wiper malware deployed against CHP plants and renewable energy systems; attack unsuccessful | Sandworm (GRU Unit 74455) | ESET, The Hacker News |
| Jan 2026 | Polish Consulate Odessa Strike | Russian missile strike on diplomatic facility | Russian military | Kyiv Post |
Marywilska Shopping Center Fire (May 2024):
On May 12, 2024, Warsaw’s largest shopping center was destroyed by arson. Polish government officially attributed the attack to GRU in May 2025:
- PM Donald Tusk: “We already know for sure that the large fire at Marywilska was the result of arson ordered by the Russian security services”
- Impact: 1,400+ shops destroyed, €500M+ damage
- Attribution basis: Lithuanian intelligence corroborated Polish findings
- Sources: Reuters, BBC, CNN
 Marywilska Shopping Center fire, Warsaw, May 2024. Source: Reuters
Marywilska Shopping Center fire, Warsaw, May 2024. Source: Reuters
 Firefighters respond to Marywilska Shopping Center blaze. GRU attribution confirmed by Polish government May 2025. Source: Reuters
Firefighters respond to Marywilska Shopping Center blaze. GRU attribution confirmed by Polish government May 2025. Source: Reuters
Railway Sabotage (November 2025):
 FSB-directed railway sabotage in Poland, November 2025. Attack carried out via recruited Ukrainian proxies.
FSB-directed railway sabotage in Poland, November 2025. Attack carried out via recruited Ukrainian proxies.
Energy Grid Attack - DynoWiper (December 2025):
On December 29-30, 2025, Sandworm (GRU Unit 74455) deployed a previously undocumented wiper malware called DynoWiper against Polish energy infrastructure. The attack occurred on the 10th anniversary of Sandworm’s 2015 Ukrainian power grid attack.
| Attribute | Details |
|---|---|
| Attack Date | 29-30 December 2025 |
| Threat Actor | Sandworm (GRU Unit 74455) |
| Attribution Confidence | Medium (ESET) |
| Malware | DynoWiper (Win32/KillFiles.NMO) |
| Malware Type | Wiper - destructive data deletion |
| Impact | Unsuccessful - no service disruption confirmed |
Targets:
- Two combined heat and power (CHP) plants
- Renewable energy management systems (wind turbines and photovoltaic farms coordination infrastructure)
DynoWiper Technical Capabilities:
- Erases files and disables system recovery mechanisms
- Removes Shadow Copies and restore points
- Designed to destabilize critical infrastructure systems
Attribution Basis:
- ESET attributed with “medium confidence due to a strong overlap with numerous previous Sandworm wiper activity”
- Links based on overlaps with prior wiper activity associated with Sandworm, particularly post-February 2022 Ukraine invasion
- ESET’s Q2-Q3 2025 APT Activity Report documented regular wiper attacks against Ukrainian targets by this group
IOC:
- SHA-1:
4EC3C90846AF6B79EE1A5188EEFA3FD21F6D4CF6 - Detection: Win32/KillFiles.NMO
Assessment: This attack represents the most significant cyber operation against Polish critical infrastructure in years. The targeting of both conventional CHP plants and renewable energy coordination systems demonstrates sophisticated operational planning aimed at cascading infrastructure failures. While unsuccessful, the attack confirms Sandworm’s continued focus on energy sector disruption in NATO countries.
Sources: ESET Research, The Hacker News, Security Bez Tabu
Telegram Recruitment for Sabotage Operations
Per OCCRP investigation, Russian intelligence services are actively recruiting European citizens via Telegram to conduct sabotage operations:
- Recruitment method: Anonymous Telegram channels offer €500-€2,000 for tasks ranging from graffiti to arson
- Target countries: Poland, Germany, France, Estonia, Latvia, Lithuania, Czech Republic
- Tasks assigned: Arson, reconnaissance, infrastructure damage, Molotov cocktail attacks
January 2026 Events
| Date | Event | Cyber Response |
|---|---|---|
| 12-13 JAN | Polish Consulate Odessa struck | DDoS surge |
| 15 JAN | Tusk attributes energy attack to Russia | Server Killers campaign |
| 17 JAN | MiG-29 transfer confirmed | ICS claims |
Targeted Organizations - January 2026
50+ Polish organizations were targeted across defense, energy, government, financial, and transportation sectors.
Consolidated Threat Actor Timeline - January 2026
Timeline of all threat actors targeting Poland, derived from Baysec CTI:
| Date | Actor | Target/Activity | Attack Type | Verification |
|---|---|---|---|---|
| 02 JAN | NoName057(16) | Poland | DDoS | Confirmed |
| 06 JAN | letchik | Polish Tax Firm | Unauthorized access | Claimed |
| 06 JAN | The Flash DDoS BOX | Poland | DDoS | Confirmed |
| 07 JAN | The Gentlemen | Wamtechnik | Ransomware | Confirmed |
| 08 JAN | Dark Storm Team | Government websites, Gas Distribution, PKP, KRUS | DDoS | Confirmed |
| 10 JAN | Yiix074 | Polish Army | Data leak | Unverified claim |
| 11 JAN | BD Anonymous | rozklad-pkp.pl, Ministry of Interior website | DDoS | Confirmed |
| 11 JAN | H4CKTHOR | Multiple Polish websites | DDoS | Confirmed |
| 12 JAN | aiyewumi | Inpost | Data breach | Unverified Claim |
| 12 JAN | Z-PENTEST ALLIANCE | Wastewater CCTV | ICS access | Confirmed |
| 13-14 JAN | NoName057(16) | 7 PGZ defense subsidiaries | DDoS | Confirmed |
| 14 JAN | HEXROOTGROUP | Polish server for players | DDoS | Confirmed |
| 14 JAN | payoutsking | Chemirol | Ransomware | Confirmed |
| 14 JAN | NoName057(16)/DDoSia | TechnoAlpin Snow Production | ICS access | Claimed |
| 15 JAN | Server Killers | Government websites | DDoS | Confirmed |
| 15 JAN | Dark Storm Team | Olsztyn-Mazury Airport | DDoS | Claimed |
| 17 JAN | BD Anonymous | BLIK | DDoS | Claimed |
| 17 JAN | thelastwhitehat | PoradnikZdrowie | Data breach | Claimed |
| 17 JAN | QuietSec | MTK-ACMO Heating Controllers | ICS access | Claimed |
| 19 JAN | QuietSec | URE, PSE, ARE (Energy sector) | DDoS | Confirmed |
| 19 JAN | Z-PENTEST ALLIANCE | Industrial Dosing Equipment | ICS access | Claimed |
| 22 JAN | QuietSec | e-podróżnik.pl, rozkład-pkp.pl (Polish travel portals) | DDoS | Confirmed |
40+ unique threat actors targeted Poland and Europe in January 2026. This timeline shows major activities.
Verification: Confirmed = independently verified; Claimed = threat actor post only; Unverified = no supporting evidence.
Source: Baysec CTI
ICS/SCADA Access Claims - January 2026
10+ claims of unauthorized access to Polish industrial control systems. Per CISA Advisory AA25-343a, pro-Russian groups are actively targeting ICS via VNC exploitation and default credentials.
| Date | Target | Actor | Risk | Verification |
|---|---|---|---|---|
| 17 JAN | MTK-ACMO Heating Controllers | QuietSec | High | Claimed (Telegram post) |
| 19 JAN | Industrial Dosing Equipment | Z-PENTEST ALLIANCE | High | Claimed (Telegram post) |
| 02 JAN | Wastewater Treatment Management | Z-PENTEST ALLIANCE | High | Assessed (TTP match) |
| 15 JAN | Water Treatment Station | Z-PENTEST ALLIANCE | High | Assessed (TTP match) |
| 12 JAN | Wastewater Treatment Plant CCTV | Z-PENTEST ALLIANCE | Moderate | Claimed (Telegram post) |
| 15 JAN | Boiler Management System | NoName057(16)/DDoSia | Moderate | Assessed (TTP match) |
Verification Key:
- Claimed = Threat actor posted evidence (screenshots/video) on Telegram - not independently verified
- Assessed = Attribution based on TTP alignment with CISA AA25-343A
Note: Z-PENTEST ALLIANCE is the primary water/wastewater sector threat actor per Cyble 2025 Threat Landscape Report. These are threat actor claims - actual ICS compromise has not been independently confirmed.
ICS Exploitation Methodology (CISA AA25-343A)
Per CISA Advisory AA25-343A, pro-Russian hacktivist groups employ the following TTP chain to compromise ICS/SCADA systems:
Attack Chain:
| Step | Technique | MITRE ID | Description |
|---|---|---|---|
| 1 | Scan for vulnerable devices | T0883, T1595.002 | Use internet-scraping tools (Nmap, OPENVAS) to find VNC services on ports 5900-5910 |
| 2 | Initiate temporary VPS | T1583.003 | Spin up disposable infrastructure to execute brute force attacks |
| 3 | Access via VNC | T1021.005 | Connect to hosts using VNC remote desktop software |
| 4 | Confirm connection | T0886 | Verify access to vulnerable device |
| 5 | Brute force credentials | T1110.003 | Use password spraying tools against default/weak credentials |
| 6 | Gain HMI access | T0883, T0812, T0859 | Access Human-Machine Interface with default or no passwords |
| 7 | Manipulate via GUI | T0823 | Use HMI graphical interface to modify system parameters |
| 8 | Cause impact | T0828, T0829, T0836 | Modify settings, disable alarms, cause loss of view |
HMI Manipulation Actions (observed):
- Modify usernames/passwords (T0892) - operator lockout
- Modify parameters and setpoints (T0836) - process disruption
- Modify device/instrument settings (T0831) - calibration tampering
- Disable alarms (T0878) - hide intrusion/effects
- Create loss of view (T0829) - force manual intervention
- Device restart/shutdown (T0816) - service disruption
Targeted Sectors (per CISA):
- Water and Wastewater Systems - Treatment facilities, distribution
- Food and Agriculture - Dairy farms, food processing
- Energy - Oil wells, heating systems, power distribution
Why These Attacks Succeed:
- VNC services exposed to internet on default ports
- Default or weak credentials on HMI devices
- Lack of MFA on critical control systems
- No network segmentation between IT and OT
- Insufficient monitoring of OT access attempts
Assessment: These actors have limited technical sophistication but cause real harm. Per CISA, they frequently misunderstand the processes they aim to disrupt, but their willingness to manipulate systems creates genuine safety risks.
Defense Industrial Base
NoName057(16) targeted 7 PGZ (Polska Grupa Zbrojeniowa) subsidiaries in 48 hours (13-14 January):
| Organization | Date | Attack |
|---|---|---|
| Polski Holding Obronny | 14 JAN | DDoS |
| DEZAMET S.A. | 13 JAN | DDoS |
| Gamrat S.A. | 13 JAN | DDoS |
| Cenzin sp. z o.o. | 14 JAN | DDoS |
| ELTA | 13 JAN | DDoS |
| Zakłady Mechaniczne Tarnów | 14 JAN | DDoS |
| OBRUM | 14 JAN | DDoS |
Assessment: Target selection suggests familiarity with Polish defense structure. Attacks caused temporary website unavailability - no data breaches confirmed.
Energy Sector
| Organization | Date | Actor | Attack |
|---|---|---|---|
| Poland’s Energy Regulatory Office (URE) | 19 JAN | QuietSec | DDoS |
| Polish Power Grids (PSE) | 19 JAN | QuietSec | DDoS |
| Agencja Rynku Energii S.A. (ARE) | 19 JAN | QuietSec | DDoS |
| Polish Gas Distribution Company | 08 JAN | Dark Storm Team | DDoS |
Government
| Organization | Attacks | Actors | Attack |
|---|---|---|---|
| gov.pl (Official Portal) | 1 | Dark Storm | DDoS |
| Ministry of Interior | 4 | Dark Storm, Server Killers, BD Anonymous | DDoS |
| KRUS (Agricultural Insurance) | 3 | Dark Storm | DDoS |
| Electronic Documents Archive | 3 | Dark Storm, Server Killers | DDoS |
| E-Dowód (Digital Identity) | 1 | Server Killers | DDoS |
| 15+ Regional governments | Multiple | NoName057(16) | DDoS |
Financial Sector
| Organization | Date | Actor | Attack |
|---|---|---|---|
| BLIK | 17 JAN | BD Anonymous | DDoS |
| TimeTax | 06 JAN | letchik | Unauthorized access |
Transportation
| Organization | Date | Actor | Attack |
|---|---|---|---|
| Olsztyn-Mazury Airport | 15 JAN | Dark Storm Team | DDoS |
| rozklad-pkp.pl | 08, 11 JAN | Dark Storm, BD Anonymous | DDoS |
| Koleje Mazowieckie | 14 JAN | NoName057(16) | DDoS |
| MPK Poznań | 06, 13 JAN | NoName057(16) | DDoS |
Private Sector
| Organization | Date | Actor | Attack |
|---|---|---|---|
| Inpost | 12 JAN | aiyewumi | Unconfirmed data breach |
| Wamtechnik | 07 JAN | The Gentlemen | Ransomware |
| Chemirol | 14 JAN | payoutsking | Ransomware |
| PoradnikZdrowie | 17 JAN | thelastwhitehat | Unconfirmed data breach |
Threat Actors
Key Groups Active in January 2026
| Actor | Attacks | Primary TTPs | State Nexus | Confidence |
|---|---|---|---|---|
| Sandworm | 1 (Dec 2025) | DynoWiper, infrastructure destruction | GRU Unit 74455 | CONFIRMED (ESET) |
| NoName057(16) | 30+ | DDoSia botnet, Layer 7 DDoS | GRU-linked | CONFIRMED (DOJ Dec 2025) |
| Z-PENTEST ALLIANCE | 5 ICS claims | VNC exploitation, SCADA access | GRU Unit 74455 | CONFIRMED (CISA AA25-343a, DOJ) |
| QuietSec | 6 | DDoS, ICS claims, data exfiltration | Pro-Russian | UNCONFIRMED |
| Dark Storm Team | 10+ | DDoS, defacement | Pro-Russian/Pro-Palestinian | UNCONFIRMED |
| Server Killers | 7 | Layer 7 DDoS | Pro-Russian | UNCONFIRMED |
| BD Anonymous | 6 | DDoS | Pro-Russian | UNCONFIRMED |
| HEXROOTGROUP | 1+ | DDoS, defacement | Pro-Russian | UNCONFIRMED |
| H4CKTHOR | 3+ | DDoS | Hacktivist | UNCONFIRMED |
| The Flash DDoS BOX | 1+ | DDoS-for-hire | Criminal (DDoS-as-a-Service) | N/A |
| Infrastructure Destruction Squad | 1+ | DDoS | Pro-Russian | UNCONFIRMED |
Confidence Key:
- CONFIRMED = Official attribution (DOJ indictment, CISA advisory, OFAC sanctions)
- UNCONFIRMED = Self-declared alignment; no official attribution
Ransomware Operators
| Actor | Victim | Date |
|---|---|---|
| SafePay | polhun.pl | 25 DEC 2025 |
| LockBit 5 | mostykatowice.pl | 30 DEC 2025 |
| THE GENTLEMEN | Wamtechnik | 07 JAN |
| payoutsking | Chemirol | 14 JAN |
Source: Baysec CTI
THE GENTLEMEN Ransomware - Detailed Profile
| Attribute | Details |
|---|---|
| Type | Ransomware-as-a-Service (RaaS) |
| Emerged | August 2025 (Trend Micro, Blackpoint) |
| Victims | 63+ across 17+ countries (Ransomware.live) |
| Model | Dual extortion (encrypt + exfiltrate) |
| Encryption | XChaCha20 + Curve25519 (Cybereason) |
| Platforms | Windows, Linux, VMware ESXi |
| CIS Restriction | Operations prohibited in Russia/CIS - indicates Russia-based operation |
| Detection | Ransomware/Win.GentlemenCrypt (AhnLab) |
Background:
THE GENTLEMEN ransomware group emerged in August 2025 and rapidly became a significant threat. Per Ransomware.live and Cybereason analysis, the group operates a sophisticated RaaS platform.
Operation Restrictions:
THE GENTLEMEN ransomware includes explicit restrictions prohibiting operations in Russia and CIS countries:
“Work prohibited in Russia and CIS countries”
This restriction is a common indicator of Russia-based or Russia-aligned ransomware operations, providing operators with protection from Russian law enforcement.
Technical Capabilities:
- Encryption: XChaCha20 stream cipher with Curve25519 key exchange
- Driver Abuse: Exploits CVE-2025-7771 (ThrottleStop.sys BYOVD - Bring Your Own Vulnerable Driver)
- Target Platforms: Windows workstations/servers, Linux systems, VMware ESXi hypervisors
- Exfiltration: Pre-encryption data theft for double extortion leverage
Poland Activity:
- 07 JAN 2026: Wamtechnik (Polish manufacturing company) - data encrypted and exfiltrated (DeXpose)
European Energy Sector Targeting:
- 26 DEC 2025: Oltenia Energy Complex (Romania) - major energy infrastructure victim (BleepingComputer)
Victim Profile (63+ total):
- Manufacturing, energy, healthcare, professional services
- Geographic distribution: Europe, North America, Asia-Pacific
- Average ransom demands: Undisclosed (negotiated per victim)
Assessment: THE GENTLEMEN represents a sophisticated, likely Russia-based ransomware operation. The CIS restriction, combined with targeting patterns focused on NATO countries and Ukraine allies, suggests alignment with Russian strategic interests. The group’s rapid victim accumulation (63+ in ~6 months) indicates effective operations and affiliate recruitment.
Source: Ransomware.live, Cybereason, Baysec CTI
Threat Actor Details
Sandworm (GRU Unit 74455) - APT44
| Attribute | Details |
|---|---|
| Type | State-Sponsored APT |
| Also Known As | APT44, Seashell Blizzard, IRIDIUM, Voodoo Bear, Telebots |
| Active Since | 2009 |
| State Nexus | Confirmed - GRU Unit 74455 (Main Centre for Special Technologies) |
| Primary TTPs | Wiper malware, ICS attacks, supply chain attacks |
| Notable Operations | BlackEnergy (2015 Ukraine grid), NotPetya (2017), Industroyer (2016, 2022) |
Background:
Sandworm is Russia’s most destructive cyber threat actor, operated by GRU Unit 74455. The group has conducted numerous attacks against critical infrastructure, most notably the 2015 and 2016 Ukrainian power grid attacks and the NotPetya global wiper attack in 2017.
December 2025 Poland Attack:
On December 29-30, 2025, Sandworm deployed DynoWiper (Win32/KillFiles.NMO) against Polish energy infrastructure:
| Target | Details |
|---|---|
| Two CHP plants | Combined heat and power facilities |
| Renewable energy systems | Wind turbine and photovoltaic farm coordination infrastructure |
DynoWiper Malware:
| Attribute | Details |
|---|---|
| Detection Name | Win32/KillFiles.NMO |
| Type | Wiper (destructive) |
| Capabilities | File erasure, Shadow Copy deletion, recovery mechanism disabling |
| SHA-1 | 4EC3C90846AF6B79EE1A5188EEFA3FD21F6D4CF6 |
Attack Outcome: The attack was unsuccessful with no confirmed service disruption. However, the attack represents the most significant cyber operation against Polish critical infrastructure in recent years.
Attribution Basis (ESET):
- Medium confidence attribution based on “strong overlap with numerous previous Sandworm wiper activity”
- Attack timing on 10th anniversary of 2015 Ukrainian power grid attack
- Consistent with Sandworm’s documented pattern of energy sector targeting
Assessment: Sandworm’s targeting of Polish energy infrastructure demonstrates Russia’s willingness to conduct destructive operations against NATO member states. While this specific attack failed, it confirms Poland as a priority target for Russian state-sponsored destructive cyber operations.
Sources: ESET Research, The Hacker News
NoName057(16)
| Attribute | Details |
|---|---|
| Type | Hacktivist Collective |
| Active Since | March 2022 |
| State Nexus | Confirmed - Russian state-sanctioned project (DOJ December 2025) |
| Primary Tool | DDoSia botnet (proprietary) |
| Channel | Telegram |
| Affiliation | CISM (Center for Study and Network Monitoring of Youth Environment) - established by order of President of Russia (October 2018) |
NoName057(16) is a state-sanctioned project whose membership includes employees of CISM (Center for Study and Network Monitoring of Youth Environment / Центр изучения и сетевого мониторинга молодёжной среды), an IT organization established by presidential order in 2018. US Department of Justice identified following facts:
- Russian government provided financial support
- DDoSia infrastructure created by CISM employees
- Cryptocurrency payments to volunteer attackers
- Targeted government agencies, financial institutions, railways, and ports
- Victoria Eduardovna Dubranova (Ukrainian national) indicted; extradited to US; trial scheduled February 2026
Rewards: US State Department offers up to $10 million for information on NoName members.
January 2026 Poland Activity Timeline:
| Date | Target | Attack |
|---|---|---|
| 06 JAN | MPK Poznań (public transit) | DDoS |
| 13 JAN | DEZAMET S.A., Gamrat S.A., ELTA, MPK Poznań | DDoS |
| 14 JAN | Polski Holding Obronny, Cenzin, ZM Tarnów, OBRUM, Koleje Mazowieckie | DDoS |
| 15+ JAN | Regional government websites (15+ targets) | DDoS |
Summary: 30+ attacks on Polish targets with concentrated 48-hour defense sector campaign (13-14 JAN)
DDoSia Operational Model:
NoName057(16) operates a crowdsourced DDoS platform where volunteers install client software to participate in attacks:
- Recruitment: Volunteers join via Telegram channels
- Registration: Users register with the bot and receive a unique ID
- Client Installation: Volunteers download and install the DDoSia client (Windows, Linux, macOS, Android versions available)
- Target Distribution: The C2 server pushes target lists to installed clients automatically
- Attack Execution: Clients generate Layer 7 HTTP floods against assigned targets
- Payment: Participants earn cryptocurrency (USDT, BTC) based on attack contribution - tracked via unique ID
- Verification: Attacks verified via check-host.net; results posted to Telegram
DDoSia Client Technical Details:
- Written in Go (cross-platform)
- Connects to C2 infrastructure for target lists
- Generates HTTP/HTTPS requests with randomized headers
- Supports proxy configuration for anonymization
- Leaderboards track top contributors (gamification)
Payment Structure:
- Volunteers paid in cryptocurrency based on “attack units” contributed
- Top performers receive bonuses
TTPs:
- Layer 7 HTTP flood attacks via volunteer botnet
- Cryptocurrency payments to DDoSia participants (~$10-50/month per active participant)
- Telegram-based target coordination and recruitment
- check-host.net for public attack verification
- GitHub used for client distribution (repositories frequently removed)
Law Enforcement:
- Europol Operation Eastwood (July 2025):
- 2 arrests (France, Spain)
- 8 arrest warrants issued
- 100+ servers disrupted across 8 countries (Poland, Ukraine, Germany, France, Netherlands, UK, USA, Switzerland)
- Source: Eurojust
- Group rebuilt infrastructure within months - operational by September 2025
- December 2025 DOJ indictments confirmed state funding and CISM employee involvement
Assessment:
| Aspect | Rating | Notes |
|---|---|---|
| Technical Sophistication | LOW | Simple HTTP floods; relies on volunteer volume, not advanced techniques |
| Organizational Capability | HIGH | Effective recruitment, payment systems, rapid infrastructure rebuild |
| Impact Potential | MODERATE | Temporary service disruption; no data theft or persistent access |
| Threat Level | ELEVATED | State backing provides resilience; nuisance-level attacks at scale |
NoName057(16) is not technically sophisticated. Their model depends on recruiting volunteers to install a simple DDoS client. The attacks are basic Layer 7 HTTP floods - no exploitation, no malware, no persistence. Any organization with proper DDoS mitigation (CDN, rate limiting, WAF) can defend against these attacks.
Their actual capability is organizational, not technical:
- Effective propaganda and recruitment via Telegram
- Gamified payment system that incentivizes participation
- Rapid infrastructure rebuild after law enforcement takedowns
- State backing provides funding and coordination
DDoSia Project - ICS Access Claims
NoName057(16)’s DDoSia Project has expanded beyond DDoS to ICS access claims, coordinating with Z-PENTEST ALLIANCE.
January 2026 ICS Claims:
| Date | Target | Risk |
|---|---|---|
| 14 JAN | TechnoAlpin Snow Production | High - Ammonia hazard |
| 16 JAN | 850kW Industrial Boiler (Czech) | High |
| 16 JAN | Clairion Clean Air Technology (France) | High - Toxic gas |
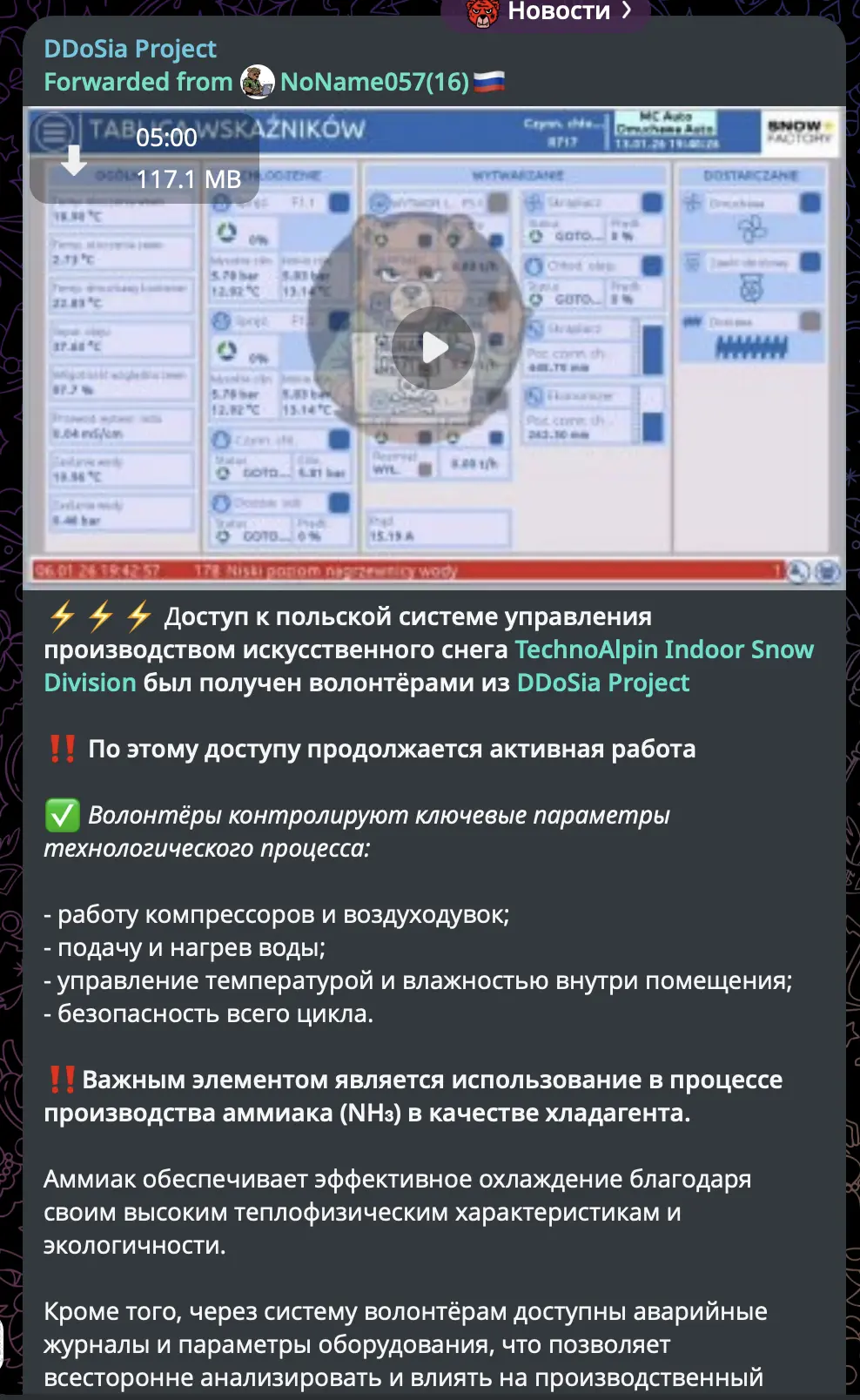 Russian-language Telegram post from DDoSia Project (forwarded from NoName057(16)) claiming access to Polish TechnoAlpin snow production system. Text states volunteers control compressors, water supply, temperature/humidity, and highlights ammonia refrigerant as critical element. Interface shows Polish-language HMI with real-time sensor data.
Russian-language Telegram post from DDoSia Project (forwarded from NoName057(16)) claiming access to Polish TechnoAlpin snow production system. Text states volunteers control compressors, water supply, temperature/humidity, and highlights ammonia refrigerant as critical element. Interface shows Polish-language HMI with real-time sensor data.
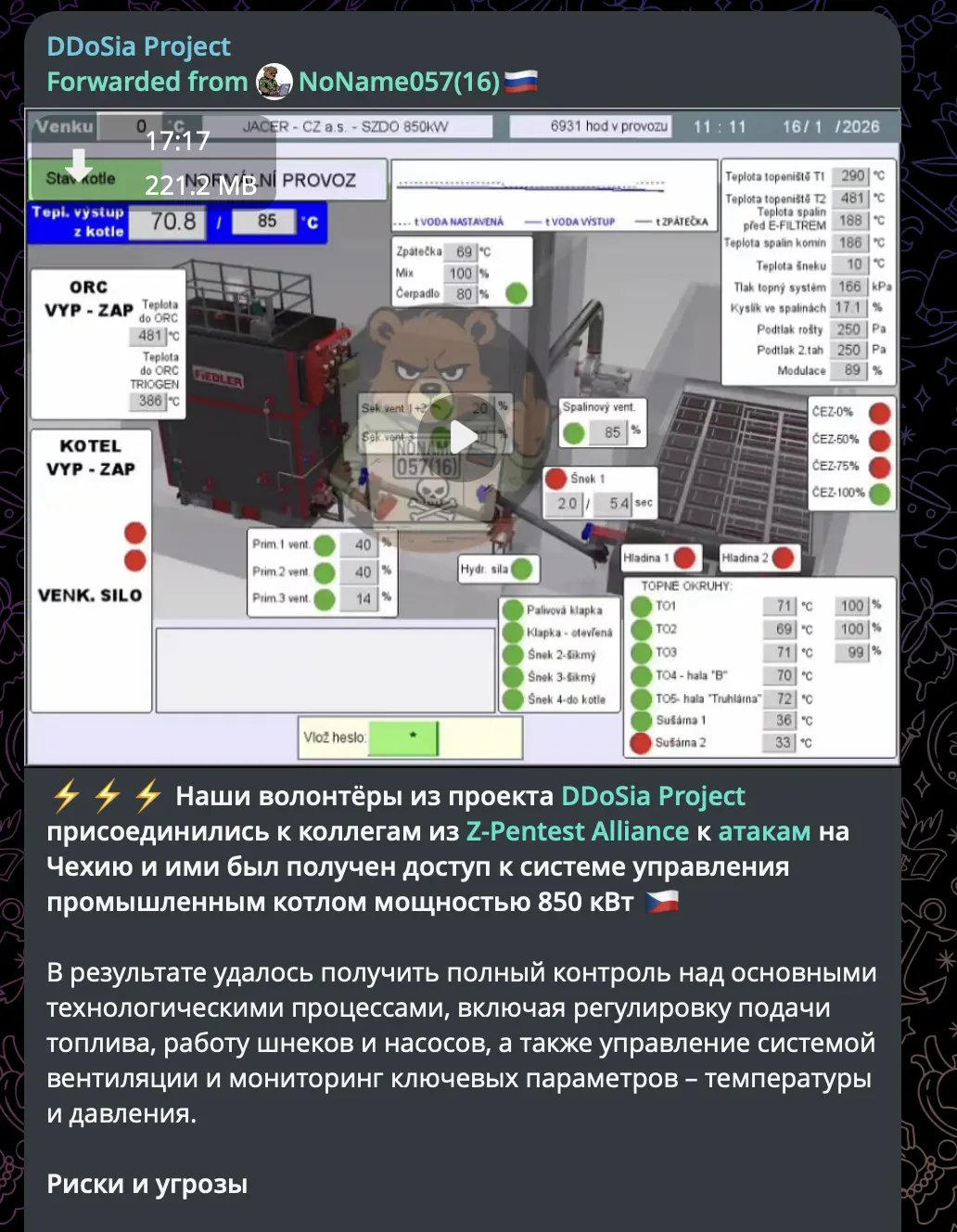 Russian-language Telegram post from DDoSia Project (forwarded from NoName057(16)) announcing collaboration with Z-Pentest Alliance on Czech 850kW industrial boiler. Text claims full control over fuel supply, augers, pumps, ventilation, and temperature/pressure monitoring.
Russian-language Telegram post from DDoSia Project (forwarded from NoName057(16)) announcing collaboration with Z-Pentest Alliance on Czech 850kW industrial boiler. Text claims full control over fuel supply, augers, pumps, ventilation, and temperature/pressure monitoring.
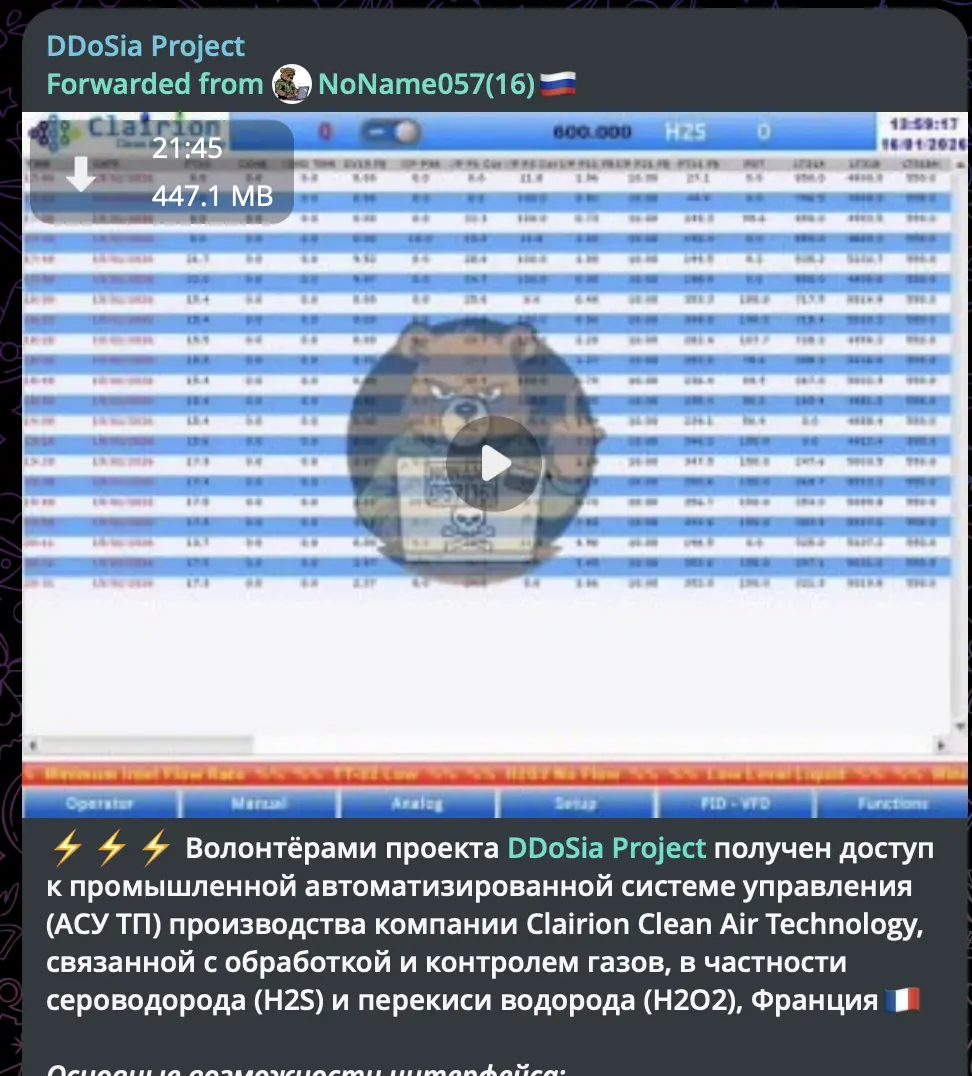 Russian-language Telegram post from DDoSia Project (forwarded from NoName057(16)) claiming access to Clairion Clean Air Technology ICS in France. System handles hydrogen sulfide and hydrogen peroxide - toxic/hazardous gases. Interface shows industrial process control data.
Russian-language Telegram post from DDoSia Project (forwarded from NoName057(16)) claiming access to Clairion Clean Air Technology ICS in France. System handles hydrogen sulfide and hydrogen peroxide - toxic/hazardous gases. Interface shows industrial process control data.
Assessment: ICS access claims show capability development. Systems with hazardous materials present safety risks if manipulated.
Source: SOCRadar, Picus Security, Baysec CTI
Z-PENTEST ALLIANCE (CARR) - GRU-Directed ICS Threat Actor
| Attribute | Details |
|---|---|
| Type | State-Sponsored ICS-focused group |
| Also Known As | Cyber Army of Russia Reborn (CARR) |
| State Nexus | Confirmed GRU - founded, funded, and directed by GRU (DOJ December 2025) |
| Primary TTPs | VNC exploitation, default credentials, HMI access, ICS manipulation |
| Coordination | Works with DDoSia Project, Nullsec Philippines |
CARR/Z-PENTEST ALLIANCE was founded, funded, and directed by the GRU (Russian military intelligence). U.S. Department of Justice identified that:
- GRU officer (“Cyber_1ce_Killer”) instructed CARR leadership on targeting
- GRU financed access to DDoS-for-hire services
- 100+ members including juveniles; 75,000+ Telegram followers
- US Critical Infrastructure attacks: Public water systems (multiple states), meat processing facility (Los Angeles - ammonia leak, meat spoilage), US election infrastructure
- Victoria Eduardovna Dubranova indicted; faces up to 27 years federal prison
U.S. Office of Foreign Assets Control Sanctions (July 2024):
- Yuliya Pankratova (leader) and Denis Degtyarenko (primary hacker) sanctioned
- Treasury confirmed: “In January 2024, CARR claimed responsibility for the overflow of water storage tanks in Abernathy and Muleshoe, Texas”
- Attacks on US critical infrastructure including water systems in multiple states
Rewards for Justice: US State Department offers up to $2 million for information on CARR/Z-PENTEST members.
January 2026 Poland Activity:
- Industrial boiler house access claim (ELTA - Zakład Automatyki Przemysłowej)
- Wastewater treatment CCTV access (12 JAN)
- Industrial dosing equipment access (19 JAN)
Observed Capabilities (from Telegram posts):
- Temperature, pressure, fuel supply control
- Auger and pump operation
- Ventilation and alarm systems
- Contact information exfiltration
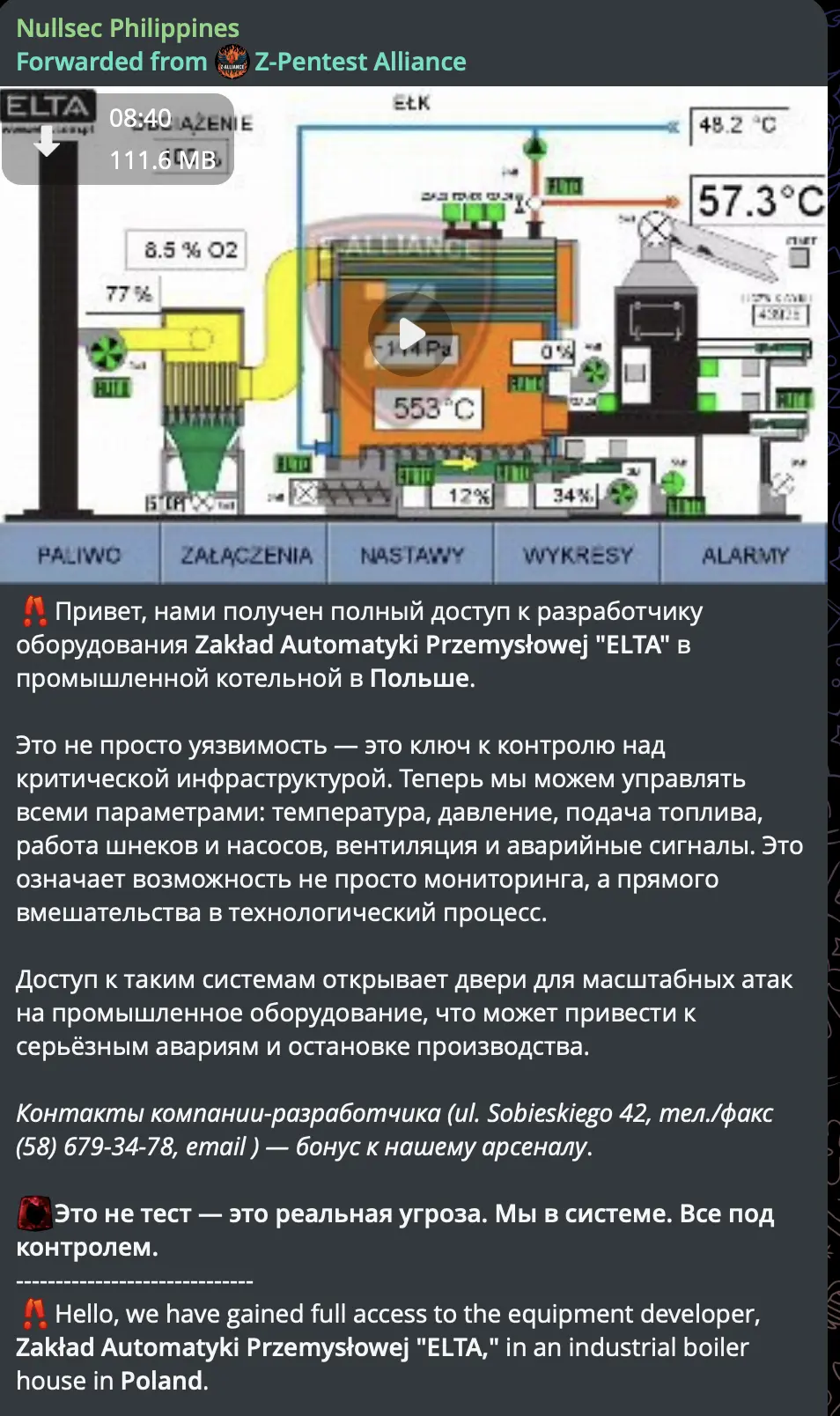 Russian-language Telegram post from Z-Pentest Alliance (forwarded via Nullsec Philippines) claiming full access to ELTA (Zakład Automatyki Przemysłowej) industrial boiler house in Poland. Text states: “We have gained full access to the equipment developer” and claims control over temperature, pressure, fuel supply, augers, pumps, ventilation, and alarm systems. Post includes developer contact information. Interface shows Polish-language HMI displaying real-time boiler parameters (553°C, O₂ levels, fuel status).
Russian-language Telegram post from Z-Pentest Alliance (forwarded via Nullsec Philippines) claiming full access to ELTA (Zakład Automatyki Przemysłowej) industrial boiler house in Poland. Text states: “We have gained full access to the equipment developer” and claims control over temperature, pressure, fuel supply, augers, pumps, ventilation, and alarm systems. Post includes developer contact information. Interface shows Polish-language HMI displaying real-time boiler parameters (553°C, O₂ levels, fuel status).
CISA Warning: AA25-343a (December 2025) specifically warned of Z-PENTEST ALLIANCE and affiliated groups targeting water, energy, and food/agriculture sectors via internet-exposed ICS.
Source: Telegram, Baysec CTI
Sector16 - Z-Pentest Affiliate ICS Group
| Attribute | Details |
|---|---|
| Type | Pro-Russian Hacktivist / ICS-focused |
| Formed | January 2025 |
| State Nexus | Possible indirect Russian government support (CISA AA25-343A) |
| Affiliation | Collaboration with Z-Pentest Alliance |
| Primary TTPs | T1078 Valid Accounts, VNC exploitation, HMI access |
| Target Countries | Italy, Portugal, Spain, Czech Republic, United States |
Background:
Per CISA AA25-343A, Sector16 is a novice pro-Russia hacktivist group that emerged through collaboration with Z-Pentest in January 2025. The group maintains a public Telegram channel where they share videos, statements, and claims of compromising critical infrastructure.
Key Intelligence:
- Members may have received indirect support from the Russian government in exchange for conducting specific cyber operations that further Russian strategic goals
- Aligns with broader Russian cyber strategies that involve leveraging non-state threat actors for certain cyber activities, adding a layer of deniability
- Communications often align with pro-Russia narratives and reflect self-proclaimed support for Russian geopolitical objectives
- Jointly claimed US system intrusion with Z-Pentest; subsequently began posting additional intrusions claiming sole responsibility
Observed Targets:
- US energy infrastructure (claimed)
- European ICS/SCADA systems (Italy, Portugal, Spain, Czech Republic)
- HMI and web-based SCADA interfaces
TTPs (per CISA):
- Uses same methodology as Z-Pentest: VNC exploitation, default credentials
- Targets internet-exposed HMI devices
- Likely received TTP training/sharing from Z-Pentest partnership
Assessment: Sector16 represents the propagation model described in CISA AA25-343A - hacktivist groups working together, amplifying each other’s posts, and sharing TTPs. The group’s emergence from Z-Pentest collaboration demonstrates how pro-Russian ICS targeting capabilities spread across the hacktivist ecosystem.
Source: CISA AA25-343A, Baysec CTI
Dark Storm Team
| Attribute | Details |
|---|---|
| Type | Pro-Palestinian/Pro-Russian Hacktivist |
| Emerged | September 2023 (Cyble) |
| Primary TTPs | DDoS, defacement |
| Channel | Telegram |
| Notable Activity | March 2025 X (Twitter) platform attack claimed (Check Point) |
| Alliance | Coordinates with Server Killers in 7-group Lithuania campaign (CyberPress) |
Profile:
Dark Storm Team emerged in September 2023 with dual Pro-Palestinian and Pro-Russian alignment. The group gained prominence after claiming responsibility for the March 2025 attack on X (Twitter). Per Cyble threat profile, the group operates across multiple Telegram channels and coordinates attacks with other pro-Russian groups.
January 2026 Poland Activity Timeline:
| Date | Target | Attack |
|---|---|---|
| 08 JAN | Government (gov.pl) | DDoS |
| 08 JAN | Polish Gas Distribution Company | DDoS |
| 08 JAN | rozklad-pkp.pl (Rail schedules) | DDoS |
| 08 JAN | KRUS (Agricultural Insurance) | DDoS |
| 15 JAN | Olsztyn-Mazury Airport | DDoS |
| Multiple | KRUS (Agricultural Insurance) | DDoS (repeated) |
Summary: 10+ attacks. Peak activity 08 JAN (5 targets in single day). Active same days as Server Killers and NoName057(16).
Source: Wikipedia, Baysec CTI
Server Killers
| Attribute | Details |
|---|---|
| Type | Pro-Russian Hacktivist |
| Primary TTPs | Layer 7 DDoS |
| Stated Motivation | Opposition to Ukraine military support |
| Activity Scale | 200+ attack reports (Dec 2025 - Jan 2026) |
| Target Countries | Poland, Czech Republic, Denmark, Belgium, Finland, UK, Germany, Norway, Spain, Italy, Kosovo |
| Alliance | Part of 7-group anti-Lithuania alliance (CyberPress) |
January 2026 Poland Activity:
| Date | Targets |
|---|---|
| 15 JAN | Government and Military websites |
| 06 JAN | PKP Intercity, Polish State Railways, Warsaw Modlin Airport, Polish Gas Company |
European Coordination (January 2026):
| Date | Country | Targets |
|---|---|---|
| 21 JAN | Czech Republic | Military Intelligence, National Security Agency, Czech Trade Inspection |
| 20 JAN | Czech Republic | Security Information Service (BIS), National Security Office |
| 19 JAN | Czech Republic | Multiple universities (Masaryk, Brno, Prague Economics) |
Server Killers operates as part of a broader pro-Russian hacktivist coalition targeting NATO member states.
 Telegram post from Server Killers announcing DDoS attacks on Polish government websites. Text states: “We attacked Poland again because of they are supporting Ukraine with military equipment.” Lists targets with check-host.net verification links: msw.gov.pl (Ministry of Interior - mislabeled as “Justice”), edowod.gov.pl (e-Services/Digital Identity). Russian flag emoji and Kremlin imagery indicate pro-Russian alignment.
Telegram post from Server Killers announcing DDoS attacks on Polish government websites. Text states: “We attacked Poland again because of they are supporting Ukraine with military equipment.” Lists targets with check-host.net verification links: msw.gov.pl (Ministry of Interior - mislabeled as “Justice”), edowod.gov.pl (e-Services/Digital Identity). Russian flag emoji and Kremlin imagery indicate pro-Russian alignment.
Timing: 15 JAN surge coincided with PM Tusk’s public attribution of December energy attack to Russia.
Source: Baysec CTI
BD Anonymous
| Attribute | Details |
|---|---|
| Type | Pro-Russian Hacktivist |
| Primary TTPs | DDoS |
January 2026 Poland Activity:
- Ministry of Interior - multiple attacks
- BLIK (Polish payment system) - 17 JAN
- rozklad-pkp.pl - 11 JAN
- Electronic Documents Archive
Coordination: Attacks on same targets as Dark Storm Team and Server Killers within 24-48 hours.
Source: Baysec CTI
QuietSec
| Attribute | Details |
|---|---|
| Type | Pro-Russian Hacktivist |
| Primary TTPs | DDoS, ICS access, data exfiltration |
| State Nexus | Unconfirmed (behavior suggests state support) |
| Capabilities | Multi-vector: DDoS, ICS/SCADA, data breaches |
| Target Countries | Ukraine, Poland, Denmark, France |
Full Activity Timeline (December 2025 - January 2026):
| Date | Target | Country | Attack Type |
|---|---|---|---|
| 22 JAN | rozkład-pkp.pl | Poland | DDoS |
| 22 JAN | e-podróżnik.pl | Poland | DDoS |
| 20 JAN | Ukrexim Bank | Ukraine | DDoS |
| 20 JAN | Oschadbank | Ukraine | DDoS |
| 20 JAN | Ukrgasbank | Ukraine | DDoS |
| 19 JAN | Polish Power Grids (PSE) | Poland | DDoS |
| 19 JAN | Energy Regulatory Office (URE) | Poland | DDoS |
| 19 JAN | Agencja Rynku Energii (ARE) | Poland | DDoS |
| 17 JAN | MTK-ACMO Heating Controllers | Poland | ICS access |
| 09 JAN | dush.com.ua | Ukraine | Data breach |
| 04 JAN | Ukrainian Government Data Portal | Ukraine | DDoS |
| 02 JAN | Charitable Foundation International Unity Movement | Ukraine | Data breach |
| 31 DEC | Financial records of Ukraine support funds | Ukraine | Data leak |
| 29 DEC | All-Ukrainian Association “Patriot” | Ukraine | DDoS |
| 29 DEC | Support Ukrainian Defenders | Ukraine | DDoS |
| 29 DEC | Unite with Ukraine | Ukraine | DDoS |
| 27 DEC | Come Back Alive | Ukraine | DDoS |
| 27 DEC | StandWithUkraine | Ukraine | DDoS |
| 27 DEC | Direct Initiative | Ukraine | DDoS |
| 24 DEC | Rennes, Toulouse, Strasbourg | France | DDoS |
| 21-23 DEC | Danish Police, Courts, Telecom, Municipalities | Denmark | DDoS |
Ukraine Targeting: QuietSec systematically targeted Ukrainian banks (Ukrexim, Oschadbank, Ukrgasbank), Ukraine support organizations (Come Back Alive, StandWithUkraine, Support Ukrainian Defenders), and conducted data breaches against Ukrainian entities (dush.com.ua, Charitable Foundation International Unity Movement, financial records of Ukraine support funds). Targets indicate anti-Ukraine motivation with intelligence collection capability.
Poland Targeting:
- Energy sector campaign (19 JAN): URE, PSE, ARE
- ICS access claim (17 JAN): MTK-ACMO heating controllers
- Transportation/travel portals (22 JAN): rozkład-pkp.pl, e-podróżnik.pl
Targeting Pattern: QuietSec follows a geographic rotation - Denmark (21-23 DEC) → France (24 DEC) → Ukraine support orgs (27-29 DEC) → Ukraine data breaches (31 DEC - 09 JAN) → Ukraine government/banks (04-20 JAN) → Poland energy/ICS (17-22 JAN). This systematic targeting of NATO countries and Ukraine suggests coordination.
Assessment: QuietSec demonstrates multi-vector capabilities (DDoS, ICS claims, data exfiltration) that distinguish it from typical single-vector hacktivists. The combination of Ukrainian banking sector targeting and systematic NATO country rotation indicates clear pro-Russian alignment. However, no government attribution exists linking QuietSec to Russian state agencies. State nexus remains unconfirmed, behavioral patterns are consistent with pro-Russian ideology but could represent independent hacktivist activity.
Source: Baysec CTI
Campaign Analysis
Coordination Evidence
The January 2026 campaign shows indicators of coordination rather than independent hacktivism:
1. Sequential Sector Targeting:
- Week 1 (01-07 JAN): Government services
- Week 2 (08-14 JAN): Defense industrial base + ransomware
- Week 3 (15-20 JAN): Energy sector + ICS probing
2. Multi-Group Same-Day Operations:
- 08 JAN: Dark Storm Team - 5 targets
- 12 JAN: 4 groups, 7+ targets
- 15 JAN: Server Killers + Dark Storm - 9+ targets
3. Geopolitical Correlation:
| Date | Event | Cyber Activity |
|---|---|---|
| 12-13 JAN | Polish Consulate Odessa struck | DDoS surge |
| 15 JAN | Tusk attributes energy attack to Russia | Server Killers 7-target campaign |
| 17 JAN | MiG-29 transfer confirmed | QuietSec ICS claims |
DDoS Campaign Assessment
Attack Volume by Actor (January 2026):
| Actor | Claimed Attacks | Primary Targets | Peak Activity |
|---|---|---|---|
| NoName057(16) | 30+ | Defense, Regional Gov | 13-14 JAN |
| Dark Storm Team | 10+ | Government, Transport | 08 JAN |
| Server Killers | 7 | Government Services | 15 JAN |
| BD Anonymous | 6 | Government, Financial | 11, 17 JAN |
| QuietSec | 6 | Energy, ICS | 17, 19 JAN |
Attack Verification:
- Actors use check-host.net for public verification
- Some claims are exaggerated or unverifiable
- Actual downtime varies from minutes to hours
Pattern Analysis: Threat Actor Coordination
Evidence of Coordination:
| Pattern | Observation | Assessment |
|---|---|---|
| Temporal clustering | Multiple groups attack same day (08, 12, 15 JAN) | Coordinated campaign timing |
| Target overlap | Ministry of Interior hit by 3 groups | Shared targeting intelligence |
| Sector rotation | Gov → Defense → Energy sequence | Planned campaign phases |
| Telegram cross-posting | DDoSia forwards Z-PENTEST claims | Operational relationship |
| Capability layering | DDoS groups + ICS groups + ransomware | Multi-vector coordination |
Communication Patterns:
- NoName057(16) and Z-PENTEST ALLIANCE share content via Telegram
- DDoSia Project forwards ICS access claims from affiliated groups
- Attack announcements often appear within hours of each other
Assessment: The campaign structure suggests central coordination rather than independent hacktivist activity.
Threat Landscape: December 2025 → January 2026
| Indicator | December 2025 | January 2026 |
|---|---|---|
| NoName057(16) | Focused on France, Belgium, Denmark | 30+ attacks on Poland |
| ICS/SCADA Claims | Not significant | 10+ access claims |
| Defense Industry | No coordinated targeting | 7 PGZ subsidiaries in 48 hours |
| Total Threat Actors | ~15 targeting Poland | 40+ targeting Poland |
Source: Baysec CTI
Dark Web Activity Summary
Polish credential data is actively traded across multiple dark web forums and marketplaces. Activity levels observed in January 2026:
| Forum Type | Activity Level | Content |
|---|---|---|
| Telegram | VERY HIGH | Breach posts, credential dumps, combolist sharing |
| Russian clearnet forums | VERY HIGH | Breach posts, credential dumps |
| Breach forums | HIGH | Combolist sharing |
| Credential forums | HIGH | Unique combo posts |
| Dark markets | MODERATE | Fresh access sales |
| Carding forums | MODERATE | Admin access sales |
| Leak repositories | LOW-MODERATE | Database leaks |
Source: Baysec CTI dark web monitoring
MITRE ATT&CK Mapping
Enterprise Techniques
| Technique ID | Name | Threat Actors |
|---|---|---|
| T1498 | Network Denial of Service | NoName057(16), Dark Storm, Server Killers, QuietSec |
| T1499 | Endpoint Denial of Service | NoName057(16), Dark Storm |
| T1078 | Valid Accounts | QuietSec, Sector16, Z-PENTEST ALLIANCE |
| T1213 | Data from Information Repositories | QuietSec, aiyewumi |
| T1567 | Exfiltration Over Web Service | thelastwhitehat, aiyewumi |
| T1486 | Data Encrypted for Impact | THE GENTLEMEN, payoutsking |
| T1583.003 | Acquire Infrastructure: VPS | Z-PENTEST ALLIANCE, Sector16 |
| T1595.002 | Active Scanning: Vulnerability Scanning | Z-PENTEST ALLIANCE, Sector16, NoName057(16) |
| T1021.005 | Remote Services: VNC | Z-PENTEST ALLIANCE, Sector16, QuietSec |
| T1110.003 | Brute Force: Password Spraying | Z-PENTEST ALLIANCE, Sector16 |
| T1591 | Gather Victim Org Information | Z-PENTEST ALLIANCE, Sector16 |
ICS/OT Techniques (per CISA AA25-343A)
| Technique ID | Name | Threat Actors | Use |
|---|---|---|---|
| T0883 | Internet Accessible Device | Z-PENTEST ALLIANCE, Sector16, QuietSec | Gain access through internet-exposed HMI devices |
| T0812 | Default Credentials | Z-PENTEST ALLIANCE, Sector16 | Build libraries of known default passwords for control devices |
| T0859 | Valid Accounts | Z-PENTEST ALLIANCE, Sector16, QuietSec | Use password guessing tools to access legitimate accounts |
| T0886 | Remote Services | Z-PENTEST ALLIANCE, Sector16, QuietSec | Leverage VNC services to access system HMI devices |
| T0823 | Graphical User Interface | Z-PENTEST ALLIANCE, Sector16, QuietSec, NoName057(16) | Interact with HMI devices via GUIs to modify control devices |
| T0816 | Device Restart/Shutdown | Z-PENTEST ALLIANCE, NoName057(16) | Turn off HMIs during intrusion |
| T0878 | Alarm Suppression | Z-PENTEST ALLIANCE, NoName057(16) | Use HMI interfaces to clear alarms caused by activity |
| T0892 | Change Credential | Z-PENTEST ALLIANCE, Sector16, QuietSec | Change HMI usernames/passwords for operator lockout |
| T0836 | Modify Parameter | Z-PENTEST ALLIANCE, NoName057(16) | Change operational device limits from HMI |
| T0855 | Unauthorized Command Message | Z-PENTEST ALLIANCE | Send unauthorized commands to control system assets |
| T0828 | Loss of Productivity and Revenue | Z-PENTEST ALLIANCE, Sector16, QuietSec, NoName057(16) | Purposefully impact productivity and create costs |
| T0829 | Loss of View | Z-PENTEST ALLIANCE, QuietSec | Change credentials preventing remote process modification |
| T0831 | Manipulation of Control | Z-PENTEST ALLIANCE, NoName057(16) | Change setpoints impacting process efficiency |
Sources and References
Government & Law Enforcement
| Source | Description | URL |
|---|---|---|
| CISA AA25-343A | Pro-Russia Hacktivists Conduct Opportunistic Attacks Against US and Global Critical Infrastructure | cisa.gov |
| DOJ December 2025 | Justice Department Actions Against Russian State-Sponsored Cyber Criminals | justice.gov |
| Europol Operation Eastwood | Global Operation Targets NoName057(16) Pro-Russian Cybercrime Network | europol.europa.eu |
| CERT-PL | Polish national CERT advisories and incident reports | cert.pl |
Think Tanks & Research
| Source | Description | URL |
|---|---|---|
| GLOBSEC | How Russia’s Hybrid Warfare Will Escalate in 2026 | globsec.org |
| IISS | The Scale of Russian Sabotage Operations | iiss.org |
| Cyble 2025 Threat Landscape | Critical Infrastructure Attacks Became Routine for Hacktivists in 2025 | cyble.com |
News & Investigative Journalism
| Source | Description | URL |
|---|---|---|
| Reuters | PM Tusk Attributes Energy Attack to Russia | reuters.com |
| Notes From Poland | Poland Confirms Russia Behind Marywilska Fire | notesfrompoland.com |
| OCCRP | Telegram Sabotage Recruitment Investigation | occrp.org |
| BBC | Poland Railway Sabotage (FSB Attribution) | bbc.com |
| Euronews | Poland Accuses Russia of Marywilska Arson | euronews.com |
| Kyiv Post | Polish Consulate Odessa Strike | kyivpost.com |
Threat Intelligence
| Source | Description | URL |
|---|---|---|
| Baysec CTI | Primary threat intelligence platform | Internal |
| ESET Research | Sandworm DynoWiper Attack on Poland Power Grid | welivesecurity.com |
| The Hacker News | DynoWiper Malware Analysis | thehackernews.com |
| Security Bez Tabu | DynoWiper - Sandworm Poland Energy Sector Attack | securitybeztabu.pl |
| Ransomware.live | THE GENTLEMEN Group Profile | ransomware.live |
| Cybereason | THE GENTLEMEN Ransomware Analysis | cybereason.com |
| SOCRadar | NoName057(16) and DDoSia Analysis | socradar.io |
| Picus Security | How NoName057(16) Uses DDoSia | picussecurity.com |
Confidence Levels:
- CONFIRMED: Multiple independent sources, government attribution
- ASSESSED: Technical indicators align with known patterns
- CLAIMED: Threat actor statement only, unverified
