
Poland Faces Coordinated Hybrid Attacks January 2026
January 2026 marked one of the most intense periods of hybrid warfare, with coordinated cyber operations targeting Poland, highlighting the growing …
Browse our complete collection of cybersecurity research, threat intelligence, and expert analysis.

January 2026 marked one of the most intense periods of hybrid warfare, with coordinated cyber operations targeting Poland, highlighting the growing …

Critical threat intelligence advisory on n8n workflow automation platform vulnerabilities: CVE-2026-21858 (Ni8mare unauthenticated RCE), …

A brief overview of geopolitical and cyber events targeting Venezuela before and after U.S. intervention in January 2026.

Analysis of CVE-2025-14847 (MongoBleed), a pre-auth memory disclosure vulnerability in MongoDB. Includes technical details, threat activity from our …
December 2025 threat intelligence - ransomware landscape, Poland-focused analysis, dark web monitoring, vulnerability exploitation, supply-chain …

Final part three of the Hello Security series dedicated to extend cyber-security awareness, performed at WGUiSW conference.
Part two of the Hello Security series dedicated to extend cyber-security awareness, performed at WGUiSW conference.

Part one of the Hello Security series dedicated to extend cyber-security awareness, performed at WGUiSW conference.

Abusing TIOCSTI to manipulate process file descriptors and execute arbitrary commands.
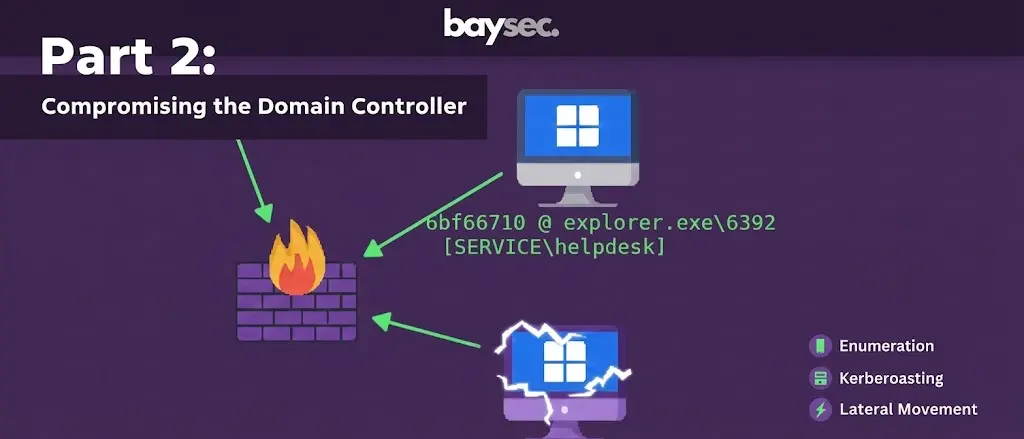
Exploiting the Active Directory environment and compromising the domain controller.
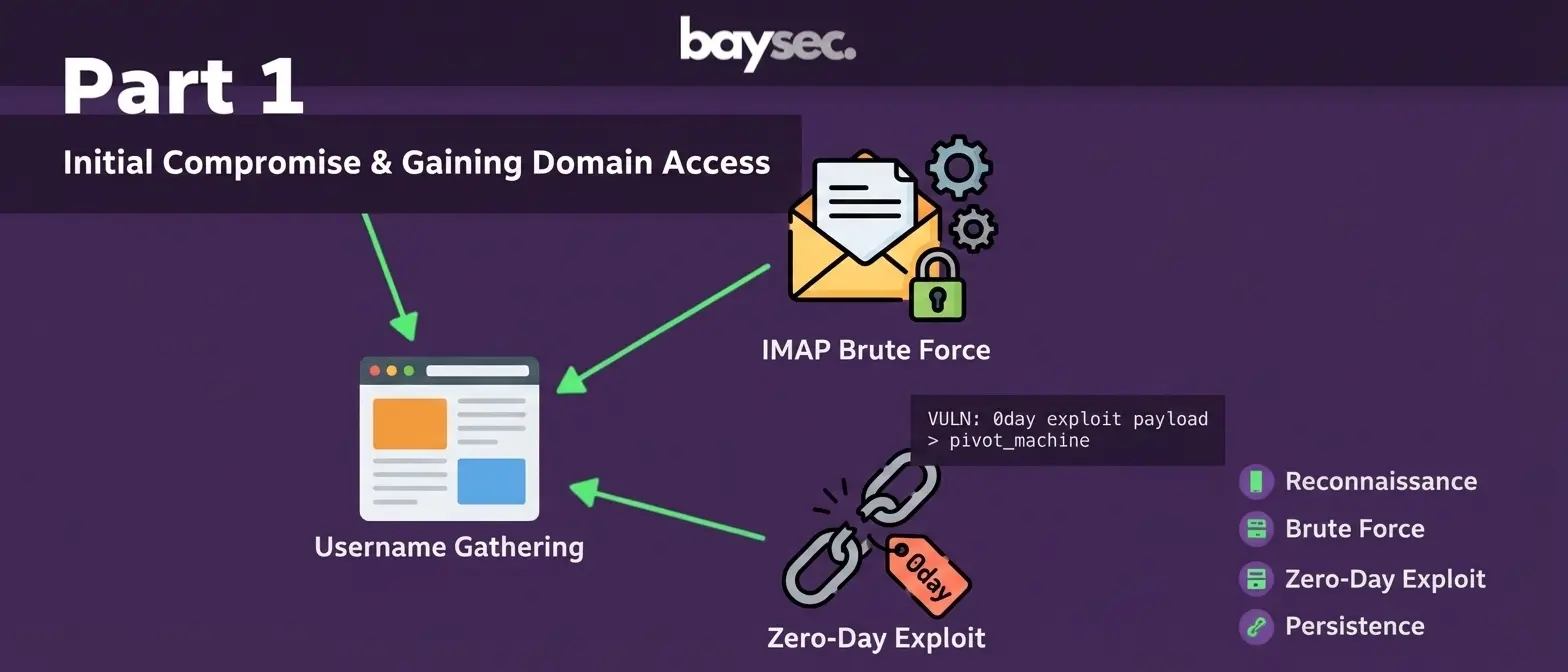
Finding a way into the internal infrastructure. Prototype pollution, popping shells, for fun, and for profit.

What happens when you run scripts without checking the contents properly?

This article will explain some of the common HTTP state interception methods.